How to Choose an Enterprise-Grade Secure File Sharing Platform
When it comes to choosing the right secure file sharing platform it can be difficult for IT teams to balance their security and compliance needs with the demands of employees who use the platform.
Despite this challenge, it’s vital for all enterprises to have this equilibrium to ensure effective collaboration without risking an incident that could lead to financial or legal problems.

Below, we’ll share with you on how to look for an enterprise-grade secure file sharing platform that allows you to achieve this balance of security and productivity.
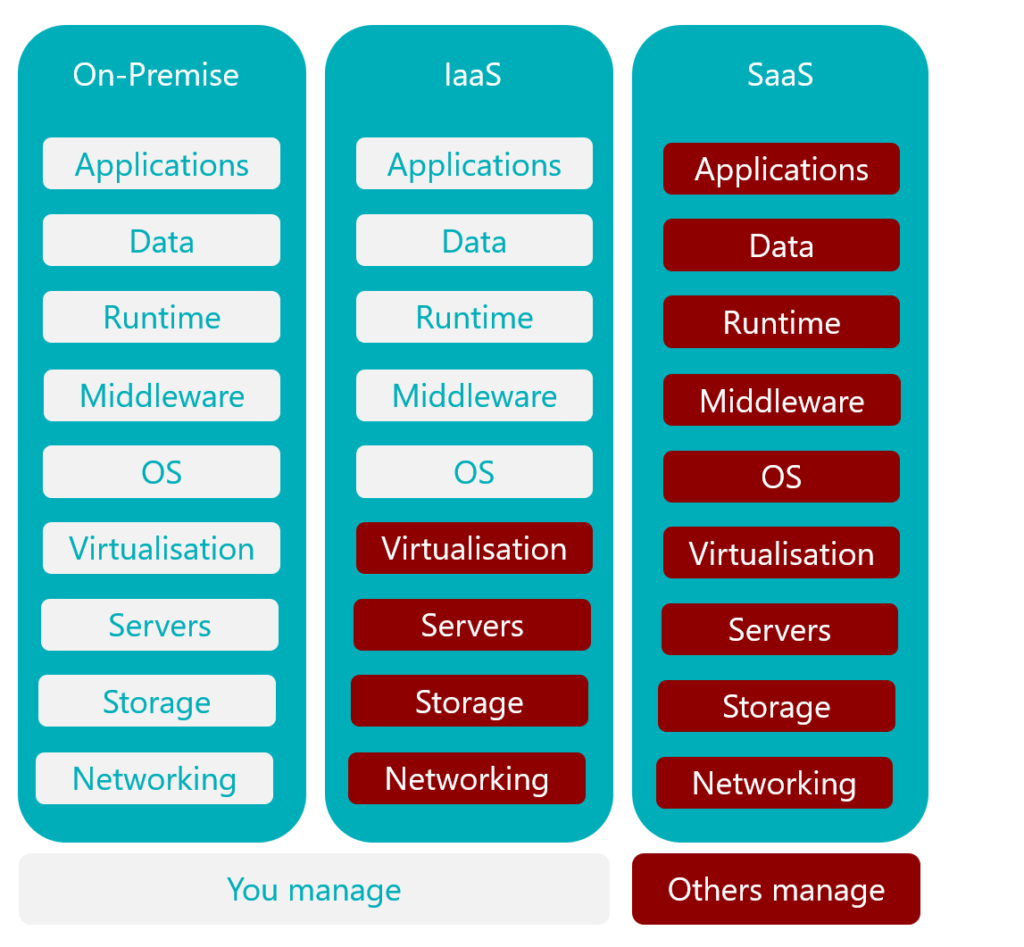
Deployment Models
When choosing an enterprise-grade secure file sharing platform, one of the first things you need to consider is different deployment models. It also takes into account who has control over the infrastructure. Deciding which deployment model you will go with, is one of the most important decisions you will make.
On-Premise
On-premise file-sharing systems give enterprises complete data ownership, residency and control. An on-premise option allows faster file sharing and doesn’t require an internet connection. You can also connect your server to the internet if you want all the features of the cloud without compromising control.
However, this option can be expensive since it requires upfront purchasing and setting up of equipment. It’s also necessary to maintain an IT team and have additional physical space for the data center.
Despite the costs, an on-premise model has the potential for greater security and easier compliance with regulations. Companies that opt for an on-premise model do so because of the sensitive nature of the information they deal with and the need to comply with regulations in the jurisdiction they’re operating in.
IaaS
According to BMC, with the Infrastructure-as-a-Service (IaaS) option, you still have complete control over your infrastructure to scale and manage your own applications, middleware and data. IaaS provides the same technologies and capabilities as a traditional data center, without the need to physically maintain and manage it—making this a fast and flexible option.
Even though the provider’s sole responsibility is to ensure the service is available and secure, there is still a dependency on the provider that you need to take into account. This model also requires internet access, which could include running into possible privacy issues due to the provider’s remote server locations.
SaaS
As for Software-as-a-Service (SaaS) options, they are highly flexible. One of the major advantages of SaaS models is the reduction in time and money spent on tedious tasks like installing, managing and upgrading software. While SaaS file-sharing platforms are recommended for smaller companies that need to launch quickly, they’re not as secure.
To have the necessary software functionality, data needs to be shared with the SaaS application servers. Transferring confidential business information to a public cloud-based SaaS service can compromise security and compliance.
Enterprise-Grade Security
What Truly Constitutes an Enterprise-Grade Solution?
When it comes to “enterprise-grade” security, a vendor’s perspective of how it defines its product to be “enterprise-grade” usually falls short in their offering and not delivering upon the non-core, yet vitally important functions that enterprises demand.
According to Ben Kepes, a former contributor to Forbes, “Enterprise-grade isn’t just about specific features, rather it is about delivering a strategy that enables a consistent architectural model with the support and service necessary for this new complex environment that organizations find themselves in.”
While this definition may sound quite vague, Kepes also shares a few key features products need to have in order to be classified as enterprise-grade.
The first is security. This requires a comprehensive approach across different infrastructures and processes. An example is a platform that has both 2FA and AES 256 Encryption.
The second is lifetime control. You should be able to maintain control of the content. Your platform should also have the option to remotely wipe the information from any device, control the file types and restrict the size of files.
The third is the user experience. Your file-sharing platform should be user-friendly and support current work processes. Employees should also be able to access files anytime, anywhere remotely, across all devices. They should also be able to receive and share files effectively and efficiently while remaining compliant with regulations.
The fourth is management policies. Organisations need to have control over policies when it comes to syncing, sharing and controlling. Since the average company shares files with over 800 different online domains, including partners and vendors, enterprises need to be able to manage internal users, customers and partners.
The fifth is the content lifecycle and role allocation. Ideally, the platform can support all stages of content and content roles. Your enterprise should be allowed to allocate content roles and enable file-sharing or file requests.
Finally, the platform has to integrate with existing IT infrastructure and minimise disruptions as much as possible.
According to Juniper Research, over 146 billion records are expected to be exposed through data breaches between 2018 and 2023. Failing to put together an effective file sharing strategy supported by an enterprise-grade secure file sharing platform can hinder your productivity and lead to serious security consequences. To begin, we recommend selecting the most appropriate deployment model for your organisation and assessing the required features in a file sharing solution.
If you’re not sure where to start, you can consult our experts which model suits your needs best. Our enterprise-grade file sharing platform can be deployed on any model that you will choose. Even if you decide to separate your intranet from the public internet. Download our free trial today.
If you enjoyed this article, please share it with your social network.